More About This Product
Knowing that your IT equipment, and more importantly that your data, is secure from physical attacks should be a primary concern. With a limited number of key combinations on traditional barrel locks and the lack of traceability, it is becoming increasingly important to provide a better solution towards rack security.
TZ Centurion rack security system
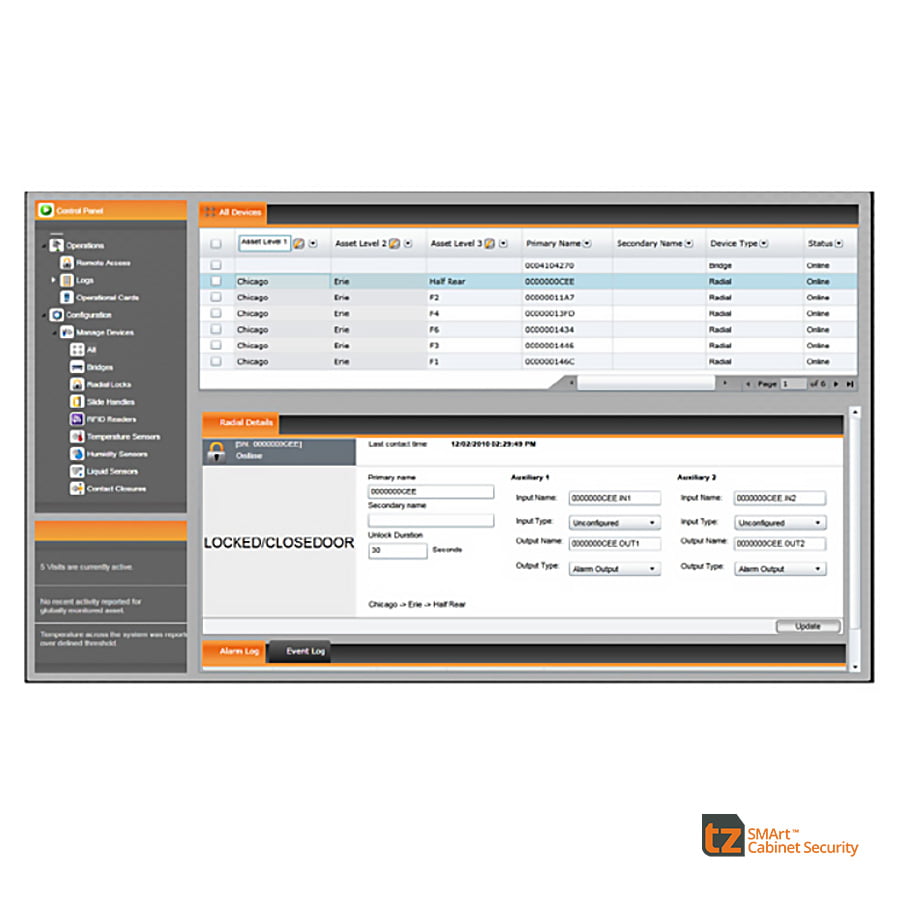
The TZ Centurion rack security system is built around a specially developed electronic security lock that has an intelligent locking engine powered by Shape Memory Alloy, which unlike many other rack security systems results in no electro-magnetic field being generated. The TZ Centurion rack security system can be accessed at rack level via proximity card, or remotely monitored and opened. This rack security solution allows IT personnel reach on to the data cabinet itself and provides an audit trail of who has opened / entered the cabinet and at what time.
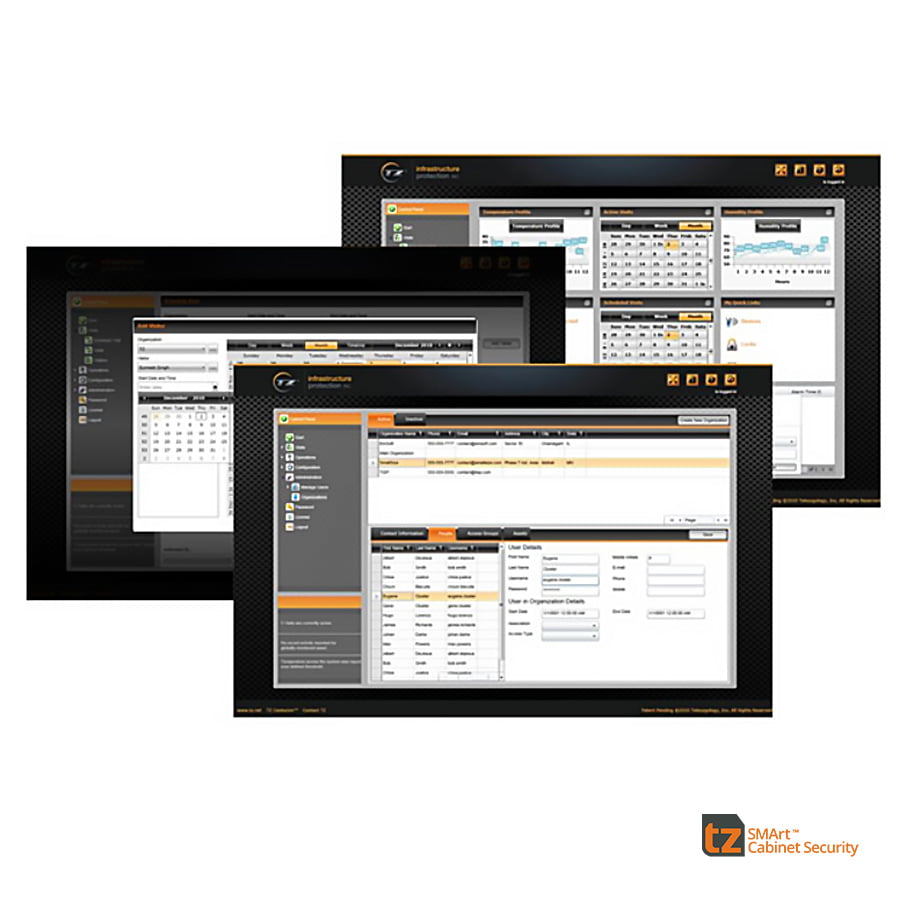
The TZ Centurion™ rack security system uses the Centurion70 Bridge to manage up to 70 TZ devices connected to each TZ Centurion™ Bridge. Each Bridge can be managed individually or scaled to a larger system allowing hundreds of networked TZ locking devices, gateways and other third party components to be administered through integrated software via web browser, the TZ Centurion™ Server software for larger installations, or through a third party network management system that supports Simple Network Management Protocol (SNMP).
TZ Centurion In-Focus Video
This video demonstrates the methods of remotely accessing IT racks via the TZ web interface and via proximity card at the rack.
Features & Benefits
Features & Benefits
- Cost effective, retrofitting and scalable rack security system.
- Uses Shape Memory Alloy locking system, with no generation of electro-magnetic field.
- Can be accessed via proximity card or remotely triggered.
- Compatible with other systems using a Wiegand data stream.
- IP address is only required for each Bridge unit, and not per component as with some systems.
- Locking devices can be daisy-chained together using Port link modules.
- Locks are powered and controlled via standard UTP CAT5e / CAT6 cabling through the TZ Centurion™ Bridge.
- In the event of a power outage cabinets remain locked, unlike systems using electro-magnetic locks which will automatically open.
- Temperature, humidity, contact and leak detection sensors available to incorporate environmental monitoring into the rack security system.
Components
Components
- Locking devices – TZ SlideHandle™ is an intelligent drop-in replacement handle for legacy manual data cabinet handles. TZ Radial is a compact, lightweight intelligent locking stud that is ideal for secure access to cabinet side doors.
- TZ Sensors – provide a cost-effective way of incorporating environmental monitoring within the TZ Centurion™ rack security system.
- Port link modules – The TZ Port Link and Multi Port Link modules provide connection for one or four TZ devices, as well as continuation of the data and power connection for the TZ network.
- TZ Centurion™ Wiegand Translator – interfaces the TZ Centurion™ rack security system to third party input devices such as card readers or biometric scanners which use a Wiegand data stream.
- TZ Centurion™ Bridge – an IP based gateway that provides power and communication to the range of TZ locking devices, sensors, readers and other components operating on a RS485 network. The TZ Centurion™ Bridge also has an integrated TZ web client which serves as the controller for small networks of devices.
- TZ Centurion™ Server – is a scalable and affordable software platform based on Microsoft RIA technology, and provides centralised remote management of the TZ Centurion™ rack security system.